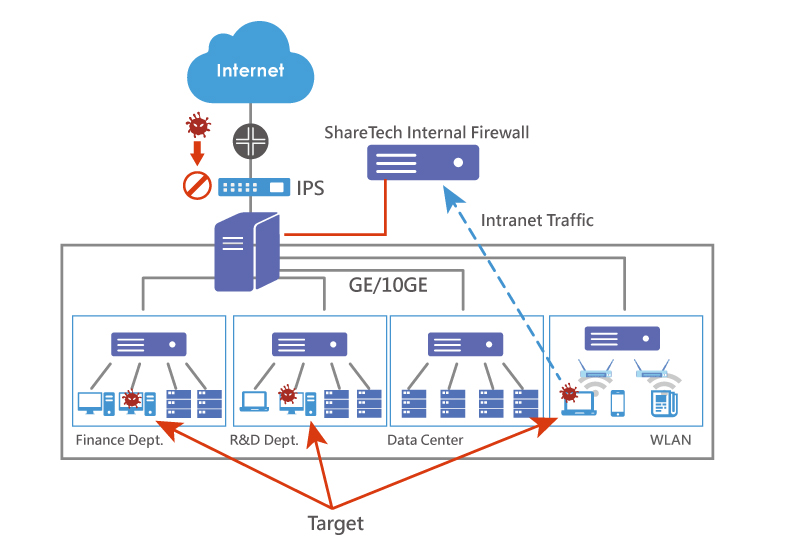
Internal Firewall
In the past few years, there has been a growing demand for internet access due to the pandemic. It gives more opportunities for hackers to illegally obtain user accounts and hack into the organization's intranets by creating phishing emails or malicious URLs on various topics. Most organizations have a basic understanding of internet security and have security devices deployed, such as firewall or UTM as gateway security, using IPS, anti-virus, anti-spam, Sandstorm, and other functions to defend against external attacks. However, the threat landscape has changed. There is a lot of focus on external network intrusions, but people seem to be ignoring the fact that the number of cyberattacks from within organizations is also increasing, making intranet security the most important issue.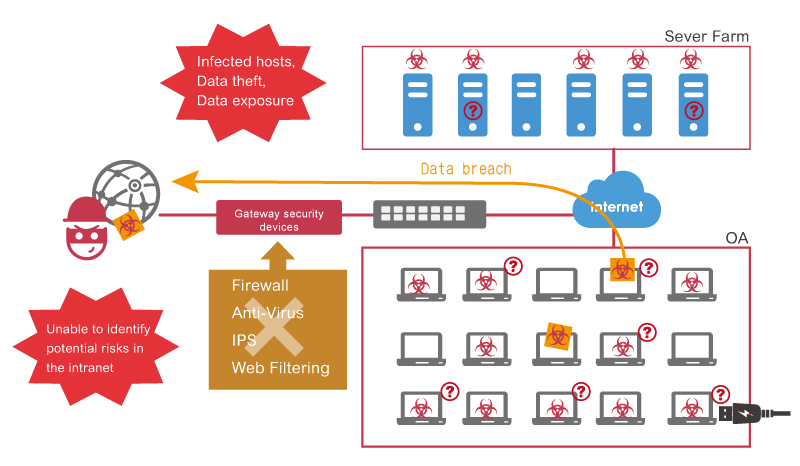
Threats to the Intranet
Malware Planted on Servers
Hackers exploit vulnerabilities in web applications or public web servers to plant malware. The more people visit the website, the faster the malware spreads.
Cyberloafing in the Workplace
Suppose IP address allocation and traffic usage are unregulated. In that case, employee productivity may decrease due to chatting online, watching stock markets, playing games, downloading videos, and browsing porn websites during working hours. It also affects the regular use of the office network.
Worm Intrusion
Worm attack patterns have diversified. Hackers may use infected USB drives, compressed files, or web directories to cause worm replication, data corruption, traffic congestion anomalies, and other problems in the LAN. If an organization with poor cybersecurity measures is attacked by computer worms but unable to take effective action, it can lead to a significant loss.
Unsegmented Networks
When employees use their personal devices to connect to the business network, hackers can easily find the exploitable part of the intranet after they intrude and gain unauthorized access. Given that most business networks are not segmented, once infiltrated, there is nothing to stop lateral movement.
Noncompliance with Security Policies
Some employees connect devices that are not allowed to connect to the internet through wireless routers or personal 4G/5G mobile Wi-Fi hotspots. Hackers can then easily bypass the gateway firewall and secretly infiltrate your system, stealing confidential information and paralyzing the network.
Remote Access Risks
The COVID-19 pandemic has made working from home (WFH) a new normal. Most employees work remotely using the Windows built-in remote desktop program or other software such as TeamViewer. However, unsecured remote connections allow hackers to easily exploit open network ports through scanning and launch brute-force attacks and credential stuffing to infiltrate business networks.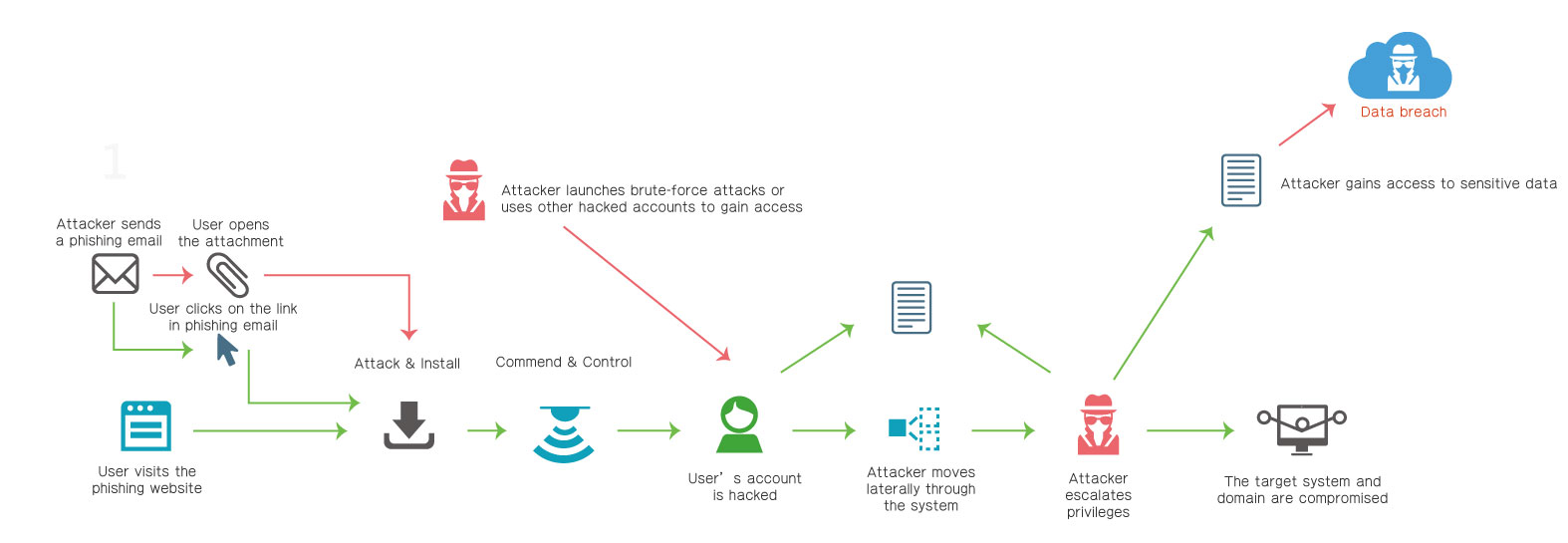
Intranet security needs an Internal Firewall
The intranet is the closest part of the network to users, yet it is the least protected. Relying only on gateway security devices would put the entire organization at risk. It is like only the entrance being protected by security, and if any criminal is negligently let in, he may do permanent damage to the entire community.
As more and more IT security incidents occur in the vulnerable segments within business networks, the previously ignored intranet security must now be re-established based on the Zero Trust model. Deploying gateway firewall is no longer enough, as it cannot effectively filter or block vulnerabilities and threats to the intranet caused by mobile devices, visitors, or with the use of wireless LANs, VPNs, IM applications, and email. Therefore, the network must be reconstructed with a second-layered and segmented defense to reduce the risk of malware spreading across different sections, organizations, and departments.