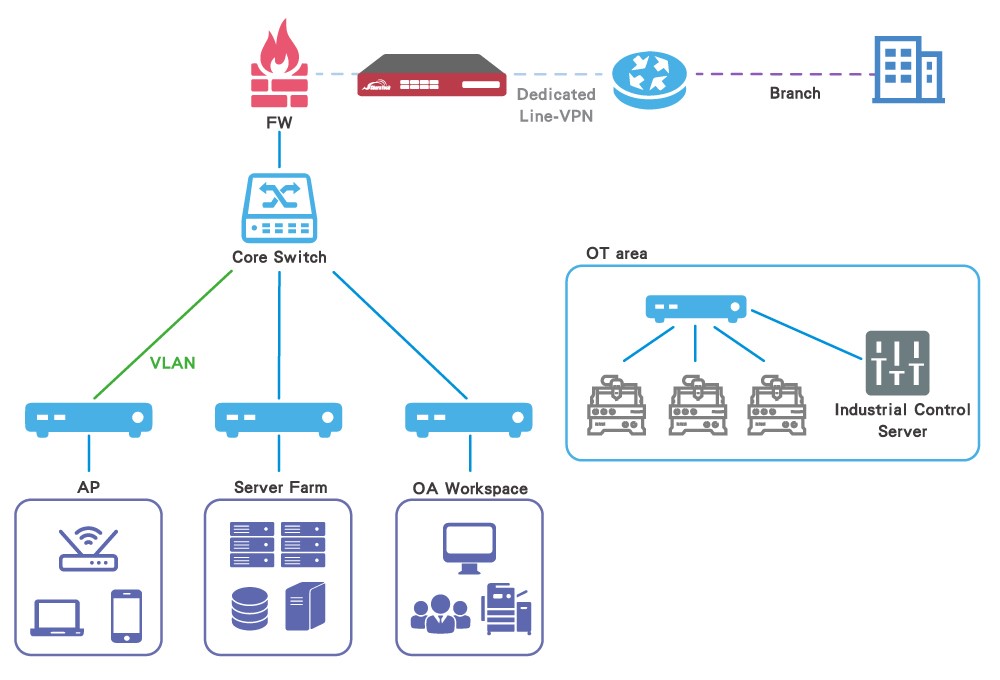
Overview
In the past few years, there has been a growing demand for internet access due to the pandemic. It gives more opportunities for hackers to illegally obtain user accounts and hack into the organization's intranets by creating phishing emails or malicious URLs on various topics. Most organizations have a basic understanding of internet security and have security devices deployed, such as firewall or UTM as gateway security, using IPS, anti-virus, anti-spam, Sandstorm, and other functions to defend against external attacks. However, the threat landscape has changed. There is a lot of focus on external network intrusions, but people seem to be ignoring the fact that the number of cyberattacks from within organizations is also increasing, making intranet security the most important issue.
With 480GB SSD and 14 GbE ports, the INF-8700C can handle sudden traffic spikes and provides Quality of Service (QoS) to ensure the stability of intranet services. The INF-8700C is equipped with 2 LAN Bypass modules, allowing packets to move straight between LANs and physically bypass the system. A built-in dashboard to increase data visibility, protect important servers from hackers, and adopt Co-Defense with wireless APs to form an integrated wired and wireless intranet security system. Centralized management includes two modes: on-premises CMS clients and ShareTech Eye Cloud, allowing administrators to manage and monitor all devices on a single platform.
When faced with the risk of advanced persistent threats and data breaches, what strategy should the business adopt?
|
Past
|
Now
|
|
|
-
Increasing number, impact, and complexity of threats
-
Zero Trust model
-
Advanced VLAN segmentation
-
Internal network segmentation to protect valuable assets
-
Increased visibility and detection capability of intranet threats
|
ShareTech New Solution: Internal Firewall (INF)
An internal firewall integrated with APs, switches, and intelligence analysis to strengthen your intranet security.
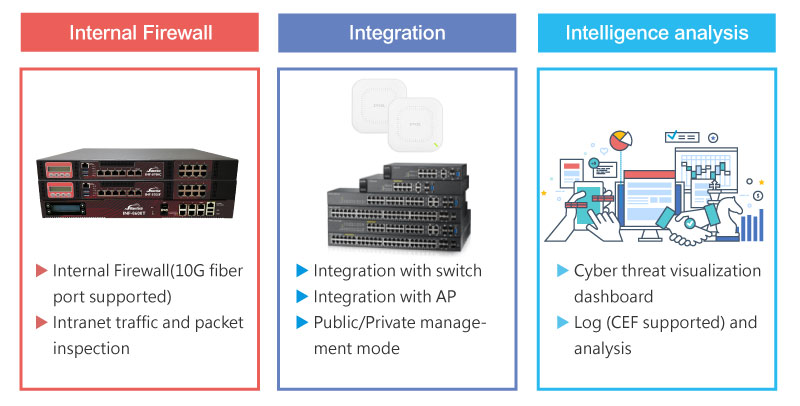
Intranet security needs an Internal Firewall
The intranet is the closest part of the network to users, yet it is the least protected. Relying only on gateway security devices would put the entire organization at risk. It is like only the entrance being protected by security, and if any criminal is negligently let in, he may do permanent damage to the entire community.
As more and more IT security incidents occur in the vulnerable segments within business networks, the previously ignored intranet security must now be re-established based on the Zero Trust model. Deploying gateway firewall is no longer enough, as it cannot effectively filter or block vulnerabilities and threats to the intranet caused by mobile devices, visitors, or with the use of wireless LANs, VPNs, IM applications, and email. Therefore, the network must be reconstructed with a second-layered and segmented defense to reduce the risk of malware spreading across different sections, organizations, and departments.
Features
ShareTech Intranet Security Solution
Reduces Concerns about Performance and Costs
In the past, there were two reasons for not considering building a second layer of protection in front of each network segment: there was not enough budget, and the traffic on the intranet far exceeded that on the internet, so if a firewall was deployed on the intranet, it might not be able to handle such a large amount of internal traffic when all detection services were enabled. Now, with the advancement of technology and the significant improvement of hardware specifications, ShareTech INF Series utilizes multi-core CPU processing and optimizes hard disk IO processing so that the internal firewall can run at high speed.
Supports Bridge Mode Only
ShareTech INF Series supports only transparent bridging mode, which is ideal for most users who do not want to change their existing architecture. The firewall protects data exchange between ports, filtering data packets between WAN and LAN. In the traditional network architecture, the intranet is managed by VLAN segmentation. As a result, there could be hundreds of VLAN segments. For this type of architecture, ShareTech INF, deployed between two switches, can filter and analyze the content of the VLAN Tag packet without any additional VLAN Tag ID settings.
Virus, IPS, Sandstorm for Intranet Traffic Filtering
ShareTech INF Series detects whether there is any abnormal behavior in the intranet and actively blocks the source of attacks with Anti-Virus, IPS, and Sandstorm. In addition to monitoring abnormal connection behavior, it is responsible for filtering viruses and reducing the attack surface.
Co-Defense with Network Switches to Enhance the Intranet Security
If endpoint devices are planted or infected with malware, hackers can infiltrate the intranet and steal resources or information. These anomalous activities will be immediately detected and blocked by the ShareTech INF Series. IT administrators can know the deployment of the switch architecture and the usage status of each node through the network topology and obtain data for dashboard analysis to further detect and identify malicious intrusion attacks.
n The Co-Defense feature keeps attackers outside the internal network when internal users are attacked by ARP or IP address spoofing. The IP address, MAC address, and attack time will be recorded for quick discovery of the infected device.
n By integrating with APs and switches, if the traffic (such as abnormal traffic, sessions, and IPS) exceeds the limit quota, the system will notify the switches and close the abnormal port to minimize the impact.
Reinforces Intranet Wireless Security
With the built-in authentication mechanism, the system filters all packets via wireless connection by virus signature detection, IPS, and Sandstorm. No need to find other wireless security solutions, achieve an effective wired and wireless network management and in-depth defense with ShareTech INF Series.
Geo IP Detection
It allows administrators to set traffic filtering policies by country or region (Location / Geo IP / Geography) and actively filter many abnormal international connections, e.g., North Korea, Philippines.
Quality of Service (QoS)
QoS provides more agile bandwidth management for industries and organizations, including maximum bandwidth, priority. It helps network administrators to manage internal network traffic, effectively reduce network congestion, and improve service and bandwidth utilization. Set a data usage and bandwidth limit, and the remaining bandwidth will be allotted to the other users according to the configuration.
Web Application Firewall (Upcoming)
Many security concerns about web applications come from the early stages of development. To perform in-depth detection, ShareTech INF Series has a built-in web application firewall (WAF), a protocol layer 7 defense, and a type of reverse proxy that protects critical servers from exposure, scanning and detecting many security vulnerabilities in web applications, such as cross-site forgery, cross-site scripting (XSS), file inclusion, and SQL injection, among others.
Dashboard
We understand the importance of log preservation. ShareTech INF Series supports CEF (Common Event Format), making it easy for administrators to manage and back up all logs. If necessary, they can use Graylog and LogServer for database queries. In addition, a built-in threat visualization dashboard in the INF-8700F provides:
n Threat Intelligence Statistics
Statistics on various threats, including viruses, spam, IPS, DoS attacks, URL control, and application control risks.
n Network Traffic Analysis
Captures all packets flowing through network switches, allowing administrators to view and search all traffic, including HTTP, SSL/TLS, Unknown, and other related traffic.
n Integrated Syslog, Flow and Dashboard
Users do not need to purchase additional traffic analysis and log management software, and the intuitive interface allows administrators to monitor and control effortlessly.
n Event Correlation Report
Event correlation reports help the system identify possible viruses or suspicious user activity based on risk data, traffic analysis, and connection status collected by ShareTech INF Series.
n Log Auditing and Querying
Track network activity by user IP, name, and application to generate more detailed and identifiable analysis reports.
n Analysis report
Administrators can customize TOP N reports, including device status, traffic analysis, mail analysis, IPS analysis, web analysis, protection analysis, application control analysis, web control analysis, Geo IP, DNS queries, and threat intelligence. Reports can be presented at various intervals (daily, weekly, monthly, or quarterly).
Central Management System (CMS) and Eye Cloud
In addition to CMS, IT administrators can also log into Eye Cloud to monitor all INF appliances, wireless APs, and switches. It is an all-in-one platform for managing various network devices deployed in either external or internal networks. When an anomaly occurs, administrators will be notified of the problem.
n Manage multiple devices on CMS, providing administrators with complete inspection and control of remote devices.
n Cloud detection system detects WEB/SMTP-related services and sends LINE or email notifications to administrators when an anomaly occurs.
n Provides detailed information, including defense ranking.
Deployment
1st Scenario: Bridge Mode can preserve the original deployment.
In bridge mode, the INF Series is designed to be as simple to deploy as possible. With little or no change to the existing configuration, internal firewalls can be easily deployed in different areas of the Intranet. Moreover, 1 to 2 pair(s) of LAN bypass is supported to guarantee Ethernet communication.
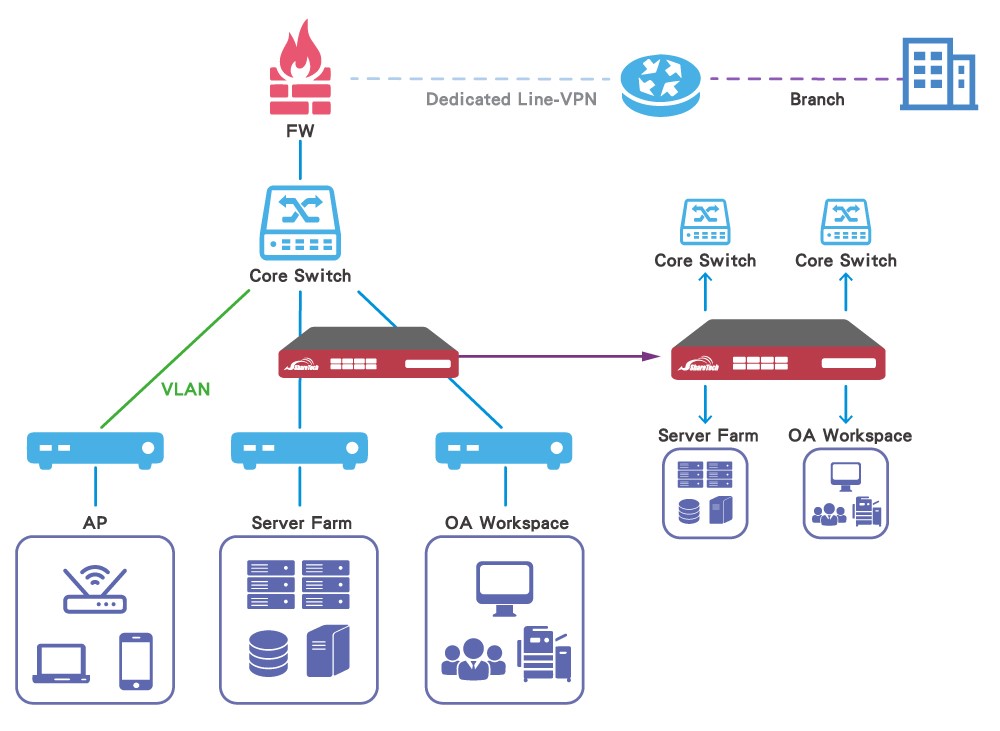
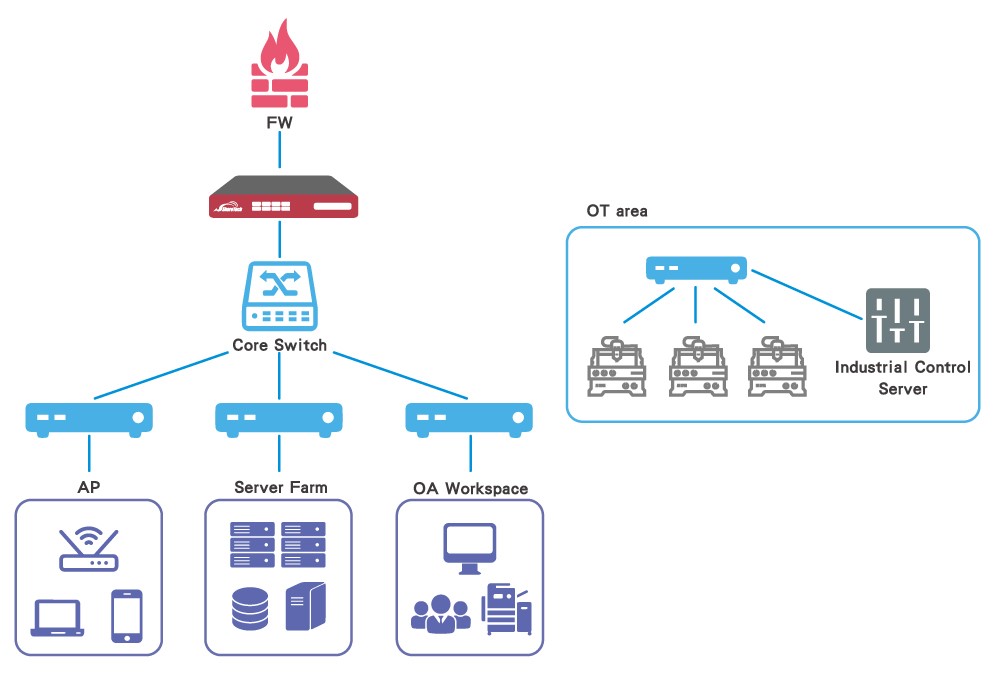
2nd Scenario: Placing the INF Series before edge switches can provide an additional layer of security.
Placing the INF Series between the core switch and edge switches can protect the Intranet by monitoring internal traffic while passing through Intranet platforms.
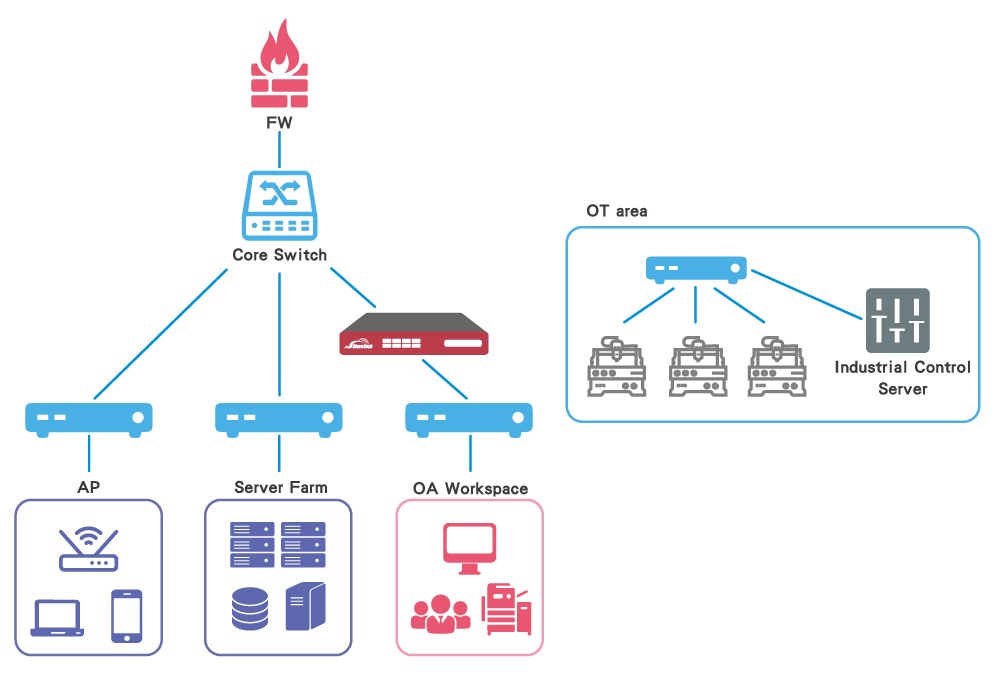
3rd Scenario: Placing the INF Series before critical servers can stay proactive with the best Ransomware protection practices.
Placing the INF Series before server farms, data centers, or workstations can prevent ransomware and other threats from entering your systems in the first place.
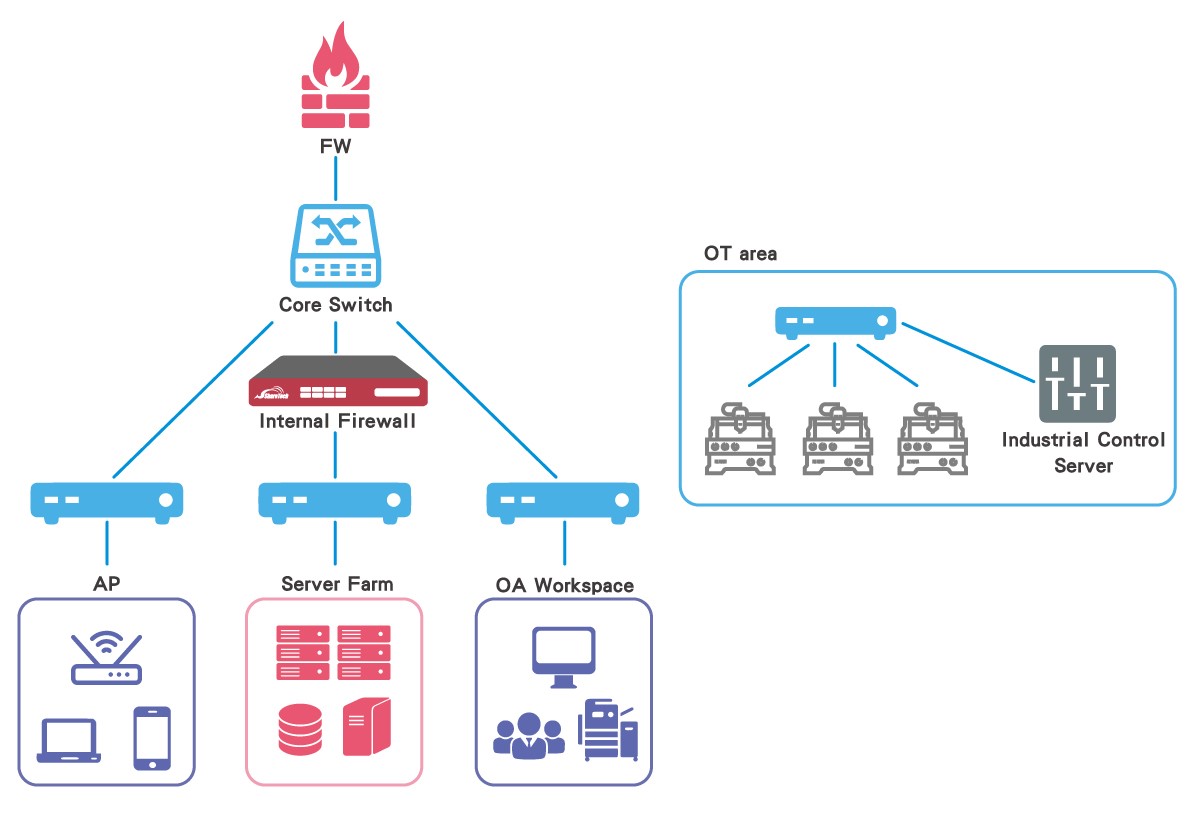
4th Scenario: Placing the INF Series before the most valuable assets can detect suspicious events and respond to incidents quickly.
Placing the INF Series before the most valuable assets—applications and data— are vulnerable to cyber-attacks. It prevents unauthorized access to critical data and malware spread through the intranet.
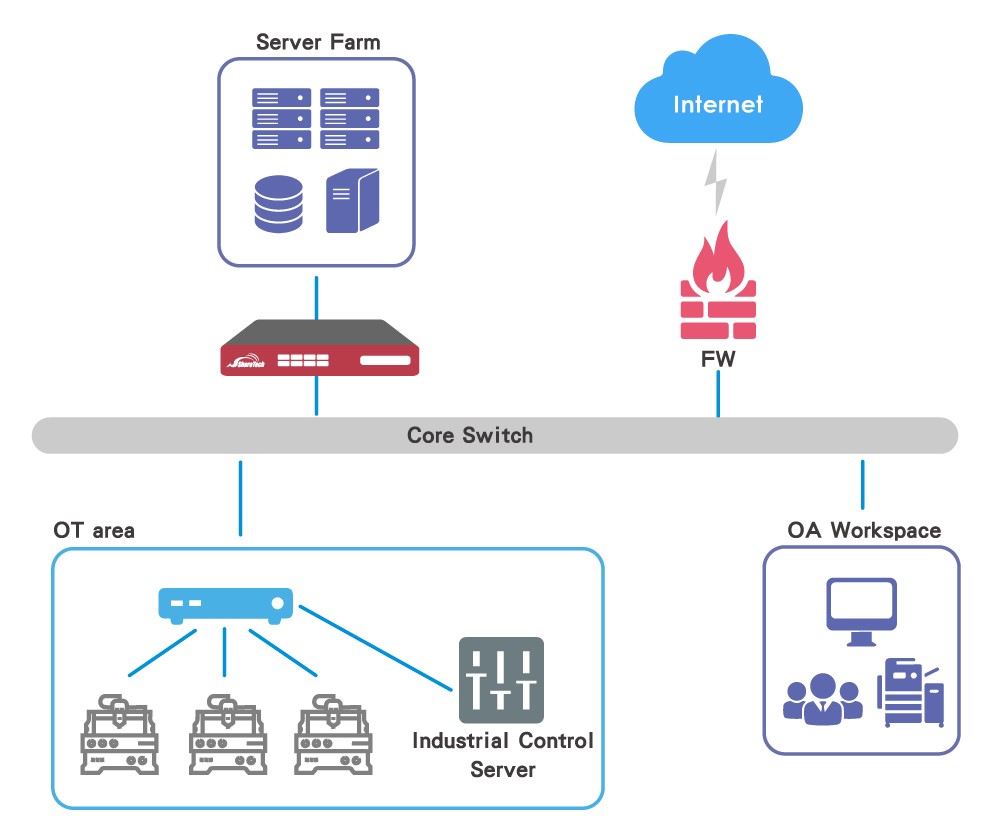
5th Scenario: Placing the INF Series after the gateway appliances can efficiently help distribute workloads across the front-end devices.
Some organizations may lack of insufficient security integration so their current gateway appliances are overloaded, causing latency and downtime due to increased traffic. Implanting the INF Series can improve operation and performance. Moreover, the built-in analytical Dashboard provides at-a-glance views of data and information.
6th Scenario: Placing the INF Series between branch locations and VPN points can filter non-secure VPN connections to protect the headquarters network.
Organizations are often slow to update their VPNs. Therefore, VPN is still liable for any damages caused.